Download is available here:
Cisco NAC Appliance Software Download PageRequires a valid Smartnet contract in order to download
4.1(2) Documentation PageSome of the feature "enhancements" that i found interesting and useful:
- NEW Cisco NAC Network Module (NME-NAC-K9) Support Release 4.1(2) introduces support for the Cisco NAC Appliance network module (NME-NAC-K9) on the next generation service module for the Cisco 2811, 2821, 2851, 3825, and 3845 Integrated Services Routers (ISRs).
The Cisco NAC Network Module for Integrated Services Routers supports the same software features as the Clean Access Server (CAS) on a NAC Appliance, with the exception of high availability. NME-NAC-K9 does not support failover from one module to another. The integration of CAS capabilities into a network module for ISRs allows network administrators to manage a single device in the branch office for data, voice, and security requirements. The NME-NAC-K9 network module is available as a single hardware module with 50-user and 100-user license options, and supports a maximum of 100 online, concurrent users.
Once initially installed, the Cisco NAC network module is managed in the CAM web console like any other Clean Access Server, and a single CAM can manage both CAS appliances and NAC network modules. To add the Cisco NAC network module to your network, at least one Clean Access Manager appliance (Lite, Standard or Super) must be already installed and configured.
Cisco ISR platforms need to run Cisco ISO software Release 12.4(11)T or later (IP Base image or above) in order to support the Cisco NAC network module.
If introducing the Cisco NME-NAC-K9 network module to an existing Cisco NAC Appliance network, you must upgrade all CAM/CAS appliances to release 4.1(2) for compatibility.
Look out for an upcoming blog entry to show how to deploy the Network Module
- NAC Appliance Platform Type Display
Now that we have Network Modules, this gives us the ability to tell whether we are looking at a NM or an Appliance. Two ways to do this:
UTILIZE THE GUI:
C
AM web console:
Device Management > CCA Servers > Manage [CAS_IP] > Network > IP | new
Platform field featuring either "APPLIANCE" or "NME-NAC"
CAS web console:
Administration > Network Settings > IP | new Platform field featuring either "APPLIANCE" or "NME-NAC"
UTILIZE THE CLI:
The CAS CLI includes the new
service perfigo platform command in release 4.1(2). The command allows you to determine whether the CAS is a standard Clean Access Server appliance or a new Cisco NME-NAC-K9 network module installed in a Cisco ISR router chassis. The command output includes either "APPLIANCE" or "NME-NAC" as the platform setting.
- Debug Log Download Enhancement
Beginning with release 4.1(2), you can now specify the number of days of collected debug logs to download in order to aid troubleshooting efforts when working with Cisco technical support. Previously, debug logs compiled to download to technical support included all recorded log entries in the CAM/CAS database. The default setting is one week (7 days).
- As always... New AV/AS Support ListTo review all enhancement, caveats and upgrade procedures please read the following release notes:
Cisco NAC Appliance 4.1(2) Release NotesPlease note that it is best practice to follow the upgrade procedures to the "T" when upgrading your NAC Managers and Servers.
For those of you just getting into the land of NACA, there is a very good presentation on the features that came about in Release 4.1(0) located on CCO called "
What's New in Cisco NAC Appliance 4.1" that should catch you up on the latest and greatest features.
 Some of the new features:
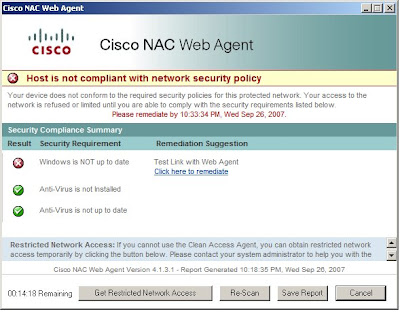
Some of the new features: This upgrade has a ton of new agent features, as you can see in the above images, so make sure to check out the release notes and read for yourself.
This upgrade has a ton of new agent features, as you can see in the above images, so make sure to check out the release notes and read for yourself.