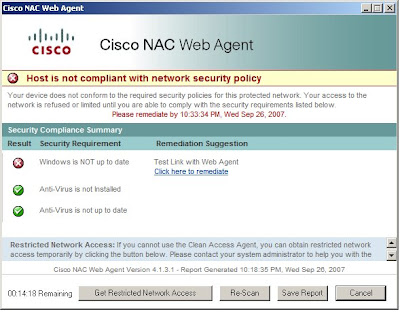
One of the much waited for features in the NAC 4.1(3) release is the NAC Web Agent. "The Cisco NAC Web Agent provides temporal vulnerability assessment for client machines. Users launch the Cisco NAC Web Agent executable, which installs the Web Agent files in a temporary directory on the client machine via ActiveX control or Java applet. When the user terminates the Web Agent session, the Web Agent logs the user off of the network and their user ID disappears from the Online Users list."
In short, it is a temporary agent that gives the ability to have a detailed posture assessment performed on a machine that it is not desired to or can't install software on.
The Spotlight:
The NAC Web Agent is a great addition to the capabilities of Cisco NAC Portfolio. The following is a functionality to agent type(CAA vs. Web Agnet) comparison. It includes some of the major benefits of each agent type to give everyone a better idea of where the new NAC Web Agent fits into their deployment.
Cisco Clean Access Agent
- Favorable end user experience - After the CAA is installed, the user does NOT have to open up a web browser every time NAC has to perform Authentication and Posture Assessment.
- Active Directory SSO - Without the CAA, internal users cannot perform ADSSO.
- Automatic Remediation - CAA walks users step-by-step through what they need to do to become compliant.
Cisco NAC Web Agent
- No Administrative Rights Required - The Web Agent only requires the rights to run Java or Active-X by the browser for it to successfully install and perform posture assessment. Some guests/visitors do not have the administrator rights necessary to install the full blown CAA, which makes the Web Agent very attractive.
- No permanent software installation - Using the Web agent takes away any chance of someone complaining of the software they downloaded at your location is the reason their computer crashed.
- Detailed Posture Assessment - The Web Agent can perform the same exact checks(Registry, File, Service, and Application) as the CAA. The only caveat is that the remediation is a manual process. The administrator may present a link to the user, but after remediation the user must click "Re-Scan" to be permitted access.
- Scan cannot be blocked by a personal firewall - As basic as this sounds, the Network Scanning capability is used a lot in the field to perform scans of guests and contractors. The problem is that a majority of users today are running some form of personal firewall rendering the network scanning useless. The NAC Web Agent is run locally on the machine to enforce posture assessment, which puts network scanning on the back burner.
Configuring Cisco NAC Web Agent:
The good news is if you have ever configured posture assessment for the CAA, then you have already configured posture assessment for the Cisco NAC Web Agent. For more information on configuring Posture Assessment, check out the CAM Installation & Configuration Guide or Cisco NAC Chalk Talk 5. The only background that should be mentioned is when creating requirements for the Web Agent it is a best practice to use a Link type requirement, so that the end user can click on the appropriate link to remediate.
The first step to enabling the web agent is to create a or modify your existing User Page. The most important option is the "Web Client (ActiveX/Applet)" setting which tells NAC which type of web agent to use or prefer. e.g. Active X or Java
The next step is to require the use of the Web Agent for the relevant Roles.
 The final step is to assign requirements to the roles that requires the web agent.
The final step is to assign requirements to the roles that requires the web agent.The end user experience:

Summary:
The Cisco NAC Web Agent is definitely going to be a highly used feature in most Cisco NAC deployments. It is fairly straight forward to understand and configure. I encourage everyone to check it out along with all the great new features in 4.1(3).
Sources: 4.1(3) Release Notes; 4.1(3) CAM Installation & Configuration Guide